Most people don’t expect to be secretly listened to in their own home. But with small, affordable devices that can blend into everyday items, live audio surveillance has become easier than ever. These tools, sometimes no larger than a USB charger, can pick up sounds around you and stream them to someone else—often without your knowledge.
In this article, we’ll walk you through:
- What live surrounding listening really means
- How these devices work and where they hide
- The signs that someone might be spying on you
If you’ve ever had a moment where someone knew exactly what you said when no one else was around, this guide may help you make sense of it—and take back control.

- Table Of Contents
- 1.What Is Live Surrounding Listening?
- 2.How Do These Devices Work?
- 3.Signs That Someone Might Be Listening
- 4.How to Check for Hidden Listening Devices
-
5.A Legal and Safer Way to Protect Your Family: What VigilKids Offers
- 6.What to Do If You Find a Listening Device
1.What Is Live Surrounding Listening?
Live surrounding listening means someone is using a device to hear what’s happening around you—in real time—without your knowledge. These devices pick up sound from your environment and send it elsewhere, often to a phone or computer controlled by the person spying.
This kind of eavesdropping isn't new, but it’s become easier and cheaper thanks to small gadgets that blend into your home and connect wirelessly. While the technology itself isn’t illegal, using it to secretly monitor others is a serious invasion of privacy—and in many cases, a crime.
People who use these devices often do so to:
- Control a partner or family member
- Check if someone is "hiding something"
- Start fights based on private conversations
- Monitor someone they don’t trust
It’s not always about high-end tech. In one Reddit thread, a user described how they suspected their partner had hidden a device in their room. The device was connected to the home Wi-Fi and seemed to be transmitting sound—enough for the partner to ask questions about conversations he shouldn't have been able to hear.
2.How Do These Devices Work?
Live listening devices come in many shapes and setups, but most work by picking up sound and sending it wirelessly to someone nearby—or storing it for later.
Here are the most common types:
-
1.Wi-Fi or Bluetooth Microphones:
- These connect to your home network or directly to someone’s phone
- They send audio live or sync it later when in range
-
2. Spy Gadgets Disguised as Everyday Items
- Examples: USB wall chargers, power strips, alarm clocks, even pens
- They often go unnoticed because they blend in
-
3. Battery-Powered Audio Recorders
- Can last weeks or even months on one charge
- Often hidden in furniture, vents, or behind electronics
- May store audio on a microSD card, picked up later
-
4. Remote-Controlled Devices
- Some can be updated or accessed by the person spying if they’re close enough
- Example from Reddit: A user believed their partner carried a laptop to sync with the device whenever nearby
This variety makes them hard to detect—especially when they don’t look like anything suspicious.
3.Signs That Someone Might Be Listening
You won’t always see the device, but behaviors can raise red flags. Many people realize something is wrong not because they find the device, but because someone else knows things they shouldn't.
Here are signs that should make you pause:
- They bring up private conversations — Things you said when you were alone
- They react quickly to plans you never told them — Like going out, watching a movie, or who you're talking to online
- They suddenly guard their own devices — No longer leaving laptops or phones around
- They get upset over vague things — Like "you’re hiding something," but they can’t say what exactly
Other clues might be more technical:
- A mystery device shows up on your Wi-Fi but you don’t own it
- Bluetooth settings show unknown names when scanning nearby
- You notice a new USB plug or charger that wasn’t there before
- Something feels "off"—like furniture moved slightly, or a cord tucked in where it wasn’t before
None of these signs prove anything alone. But when several start adding up, it’s time to take a closer look.
4.How to Check for Hidden Listening Devices
If you suspect someone might be listening to you, you don’t need expensive equipment to start looking. There are a few simple ways to investigate using tools you already have.
Here’s where to start:
Check Your Wi-Fi Network
Most live listening devices connect to the internet to send out audio.
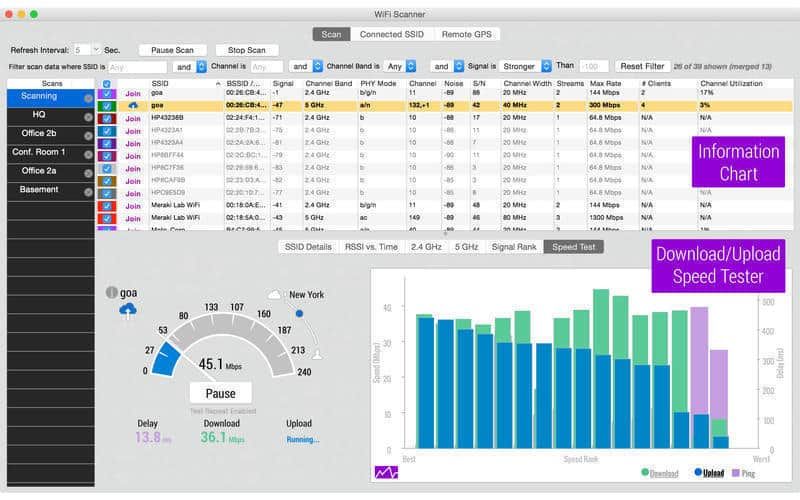
- Step 1.Log in to your router’s settings (usually through a web browser)
- Step 2.Look for any unfamiliar devices on the list
- Step 3.If you see something with a strange name or unknown MAC address, take note
You can use free tools like Fing or WiFi Analyzer to scan all connected devices and see their signal strength. A strong signal in one corner of the room could point to a hidden gadget.
Check for Bluetooth Devices
If the device doesn’t use Wi-Fi, it might be using Bluetooth.
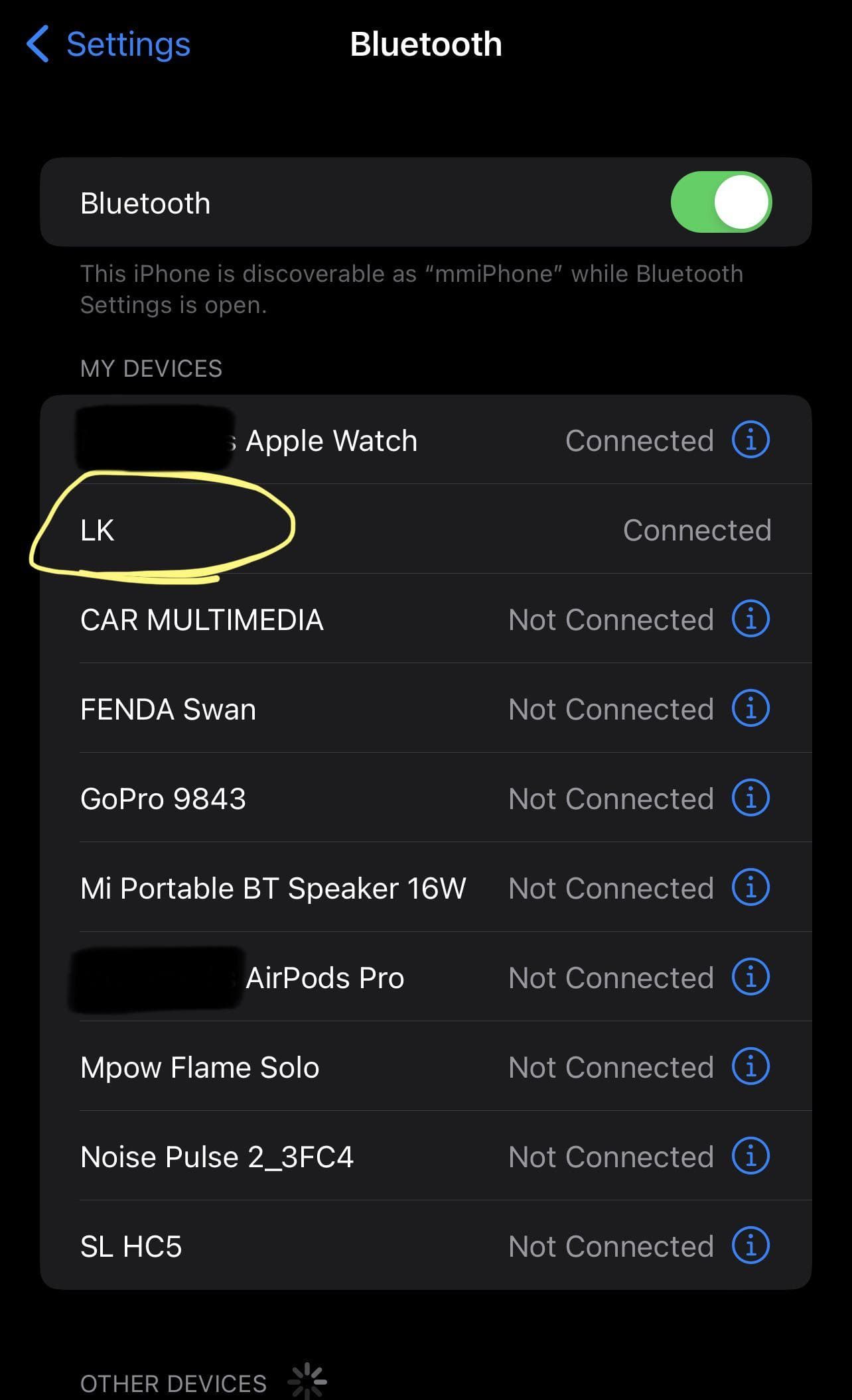
- Step 1.Open your phone’s Bluetooth settings
- Step 2.Scan for unknown nearby devices
- Step 3.Look for names you don’t recognize or anything labeled as "Audio," "Mic," or similar
Look Around Carefully
Sometimes the simplest method is the best: a visual and physical check.
- Step 1.Inspect power strips, USB ports, wall chargers, and alarm clocks
- Step 2.Look for new objects or plugs you didn’t place
- Step 3.Pay attention to dusty areas—anything recently moved or placed will leave marks
A Reddit user mentioned discovering the spy device was likely drawing power from a hidden USB cable behind their computer. Dust patterns and cable bundles are great clues if something seems out of place.
Other Helpful Tools
If you're ready to dig a bit deeper, here are a few more tools worth knowing:
- mac2vendor.com: Enter the MAC address of a suspicious device to check its manufacturer. This can help you figure out what kind of gadget it might be.
- Wireshark: A powerful (but technical) tool that lets you see where network data is going. You can use it to capture traffic and look for suspicious patterns.
- Bluetooth Triangulation Apps: Some apps let you measure Bluetooth signal strength from different spots in the room to help you find the physical location of the device.
- Block by MAC: If you're sure a device is suspicious, most routers let you block it by MAC address. This will prevent it from using your Wi-Fi at all.
5.A Legal and Safer Way to Protect Your Family: What VigilKids Offers
It’s important to remember: there’s a difference between spying and protecting.
If you’re a parent trying to keep your child safe online, you don’t need to use shady tools or hidden devices. Tools like VigilKids are made for families who want to monitor responsibly and legally.
Here’s what makes VigilKids different:
- Only for family use: Designed for parents or legal guardians
- Built on consent: Should be used with your child’s knowledge and agreement
- Focused on digital safety: Lets you understand what apps your child uses, who they message, and how long they spend on their phone
- No secret spying: It doesn’t record without permission or allow you to listen in secretly
Whether you’re worried about online strangers, bullying, or screen time, VigilKids helps open conversations—not cause conflict. It gives parents peace of mind, while respecting their child’s growing independence.
- VigilKids is not made for spying on partners, roommates, or anyone without consent. Using surveillance tools without permission is often illegal and can seriously damage trust.
6.What to Do If You Find a Listening Device
If you’ve spotted a suspicious device or have good reason to believe someone is listening, it’s time to take action—carefully and calmly.
Here’s what to do:
- Take photos or videos of the device for proof
- Do not confront immediately — removing it too soon might warn the person who planted it
- Change your Wi-Fi password — to cut off remote access
- Talk to someone you trust — a friend, a counselor, or a support group
- Contact the police or a local cybercrime unit if you feel unsafe
You should also:
- Check other areas like your car or office for similar devices
- Log out of shared accounts and change your passwords
- If needed, consider a temporary stay elsewhere while you sort things out
As one Reddit commenter said
"There is no bottom with these types." People who cross this line may not stop at one device. It’s important to stay safe and think long-term.
7.Final Thoughts: Stay Aware, Stay in Control
Feeling like someone might be listening to you is upsetting—and sometimes even scary. But you're not powerless. With the right tools and a clear head, you can take steps to protect your privacy and understand what’s really going on.
The truth is, technology has made it easier than ever for people to cross boundaries. Whether it’s a hidden microphone, a Wi-Fi-connected device, or a misused app, the line between "checking in" and "spying" can get blurry. But that line still matters—and it’s one worth defending.
Here’s what to remember:
- Trust your instincts, especially if things don’t add up
- Look for both technical clues and behavioral changes
- Document what you find, and don’t rush to confront
- Most importantly, make sure your response stays safe and legal
If you’re a parent worried about your child’s digital life, the answer isn’t hidden devices or secret recordings. It’s open conversations and responsible tools—like VigilKids. When used with care and consent, it helps families stay connected, informed, and protected.
Privacy shouldn’t be a luxury. It’s something everyone deserves—especially in their own home.
